- Multiple browser profiles
- Workflow optimization
- Team collaboration
- Synchronized browser profiles
- User-friendly
Find Every Fingerprint Leak with BrowserLeaks
Use BrowserLeaks to reveal what your browser is exposing behind the scenes. Incogniton helps you create truly isolated browser profiles. BrowserLeaks tells you if they’ll hold up under real-world scrutiny.
- Trusted by 1 million+ users

Your Browser Reveals More Data Than You Realize
Browser profiles leak data and can expose your online identity. This can lead to failed login attempts and even banned accounts. Anti-detect browsers help mask your digital fingerprint and create isolated profiles, but how natural does these look? That’s where BrowserLeaks comes in.

Test Your Anonimity in Seconds with BrowserLeaks
BrowserLeaks shows you exactly what data your browser is leaking. When used in Incogniton, it becomes your personal fingerprint audit tool. Check your:
- Canvas and font rendering hashes
- GPU model and WebGL renderer
- WebRTC IP leaks
- Timezone, language, and geolocation coherence
- Hardware and JavaScript environment details
Any leaks or other weak points revealed? Fine-tune your Incogniton profile until it looks 100% human and undetectable.
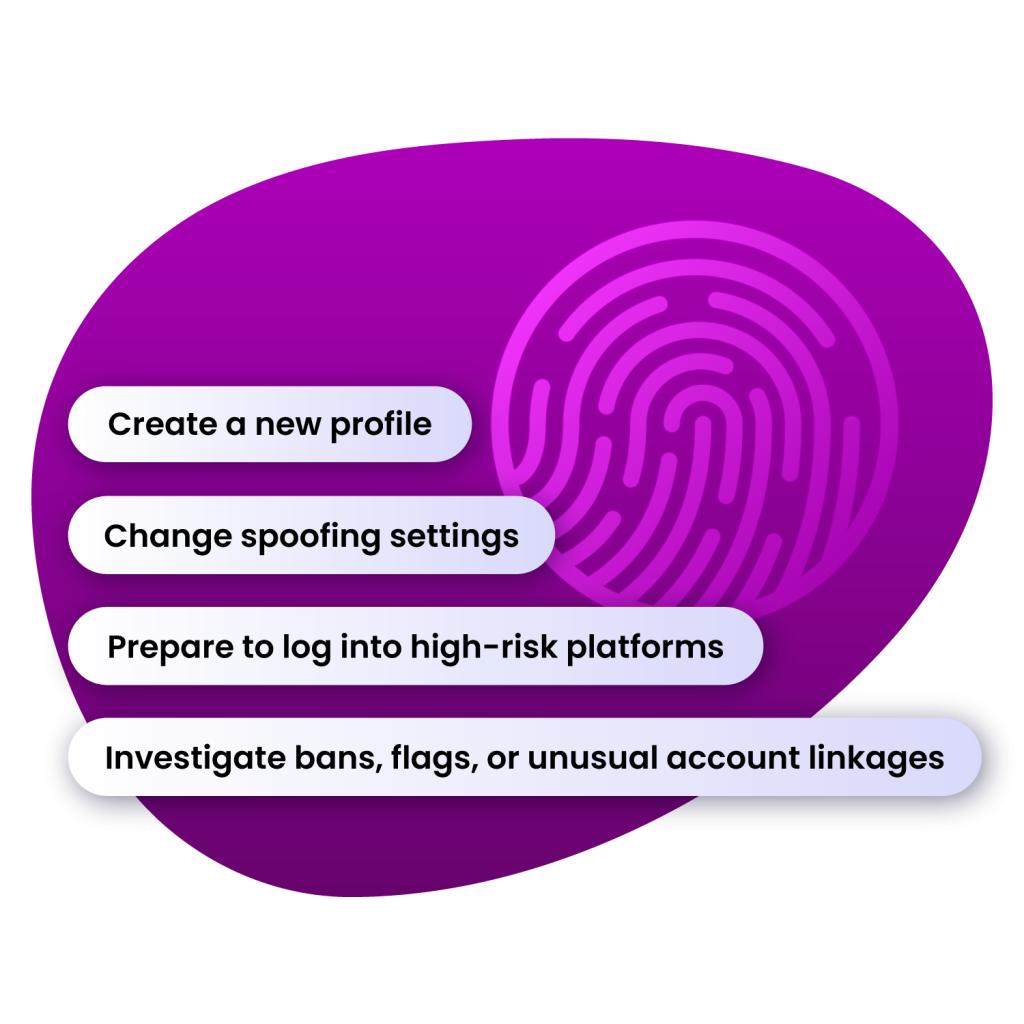
When to Run a BrowserLeaks Test
BrowserLeaks is most valuable when you:
- Create a new profile
- Change spoofing settings
- Prepare to log into high-risk platforms
- Investigate bans, flags, or unusual account linkages
Audit Your Browser Fingerprint in 5 Simple Steps

1. Prepare profiles
Set IP, timezone, language, and hardware parameters for each profile.

2. Visit test pages
Key URLs to check are Canvas, WebGL, WebRTC, IP and JavaScript.

3. Record Results
Use a spreadsheet to log hashes, GPU strings, IPs, and settings per profile.

4. Compare profiles
Look for repeated hashes, mismatched geolocation data, or VM fingerprints.
5. Adjust and retest
Tweak settings in Incogniton until each profile has a distinct, realistic fingerprint.

Why Incogniton Complements BrowserLeaks
Full profile control
Full control over cookies, user agents, WebGL, timezone, and more.
See what websites see
Discover how websites see your browser profile and digital fingerprint.
Detect hidden leaks instantly
Find mismatches across settings and know exactly which identifiers expose you.
Fix issues right away
Adjust profiles settings in just a few clicks in your Incogniton account and re-test in seconds.
Start For Free Today
Sign up now and get 10 browser profiles for FREE – no credit card required.
Frequently Asked Questions
Is BrowserLeaks.com free?
Yes. It’s a public tool. You do not have to subscribe, pay a fee or set up an account, or download a software file to use it.
Does BrowserLeaks.com store my fingerprint data?
No. According to the site’s privacy approach, all tests are run locally in your browser, and the data is not stored on their servers.
Can BrowserLeaks.com help me hide my fingerprint?
Not directly. It’s a testing tool, not an anti-detect or privacy tool. However, it can help you verify whether your current setup (e.g., VPN, anti-detect browser, or privacy extensions) is working as intended.
Who should use BrowserLeaks.com?
Anti-detect browser users, affiliate marketers, social media managers, penetration testers, journalists, OSINT researchers—anyone who needs to manage or protect their online identity.
Which browsers work with BrowserLeaks.com?
BrowserLeaks.com works on most modern browsers, including Chrome, Firefox, Safari, Edge, and privacy-focused browsers like Brave.
Will BrowserLeaks.com tell me if I’m 100% anonymous?
No. No tool can give you a “100% anonymous” score. Instead, it will show you what data you are leaking so you can take steps to minimize your fingerprint.
How does browserleaks.com compare to other tools like Pixelscan.net or Whoer.net?
BrowserLeaks.com is more of a raw, technical diagnostic tool with minimal UI, while tools like Pixelscan and Whoer.net offer more user-friendly scoring systems and consolidated results.
How often should I run tests on BrowserLeaks.com?
Run a test whenever you change your browsing setup—such as switching browsers, adding new privacy extensions, or configuring an anti-detect tool—so you can verify the changes are effective.
Can I use BrowserLeaks.com on mobile devices?
Yes, it works on mobile browsers too, though some fingerprinting elements may display differently compared to desktop.
Why do fingerprint test results differ between sites?
There are different methods of fingerprinting, and most websites use a different assortment of these methods. Some focus on JavaScript data, others on HTTP headers or network details. Also, VPNs, proxies, extensions, and IP reputation lists can also cause variations.
Do extensions affect your browser fingerprint?
Extensions can help block fingerprinting, but they can also make you more trackable. Some block certain scripts—reducing the amount of data collected—but also leave obvious gaps that make you stand out. Others add unique headers or modify your browser behaviour in detectable ways.