In a prior article, we explored how to use Whoer.net to test your anti-detect browser setup. Whoer is a great starting point for beginners—it helps identify obvious IP leaks, DNS mismatches, and basic browser fingerprint inconsistencies. But while it if you’re serious about anonymity or running complex multi-account operations, you need something more sophisticated.
And that’s what this article is about, a more advanced complement. In the following paragraphs, we’ll dive into exactly how Pixelscan works, what it tests, and how to use it to improve your browser fingerprint, especially when building and managing profiles.
What Is Pixelscan.net?
Pixelscan is a free platform that runs checks to show what websites can detect about your browsing setup. It offers an easy and reliable way to make sure your setup won’t raise red flags when managing multiple accounts, running automation, or operating at scale.
Unlike simpler tools like Whoer.net or IP leak checkers, Pixelscan goes much deeper. It evaluates and audits your browser environment across several categories that are highly relevant to fingerprint detection systems. So it is not just looking at your headers or IP—it’s analyzing how real and cohesive your setup appears.
Here’s a breakdown of the major areas it tests:
1. Canvas Fingerprint & Rendering Noise
Your browser renders a hidden graphic in the background, and the resulting hash is unique to your hardware and software. Pixelscan checks if your canvas fingerprint looks identical across profiles (a sign of spoofing) or if rendering noise is missing entirely (a sign of automation or manipulation).
2. Audio Fingerprint
Using the AudioContext API, Pixelscan measures how your browser processes sound, even if you don’t hear it. Minor variations can uniquely identify your machine. A missing or default value could signal tampering.
3. WebGL Properties & Vendor Consistency
Pixelscan evaluates your WebGL fingerprint, including GPU vendor, renderer strings, and supported extensions. If your browser claims to be running on a MacBook Pro but lists a virtual GPU or Windows-only extension, that’s a red flag.
4. Browser and OS Headers
This includes user-agent, accept-language, encoding, and platform strings. These need to match the rest of your fingerprint. For example, if your user-agent says “Windows” but your screen dimensions look like a mobile device, you’ve got a problem.
5. Timezone and Language Mismatch
If your language is set to en-US but your timezone is in Europe or Asia, Pixelscan will flag it. Platforms notice this too—it’s often a sign of spoofing or proxy use.
Why Pixelscan Matters for Multi-Accounting and Anti-Detect Browser Users
If you’re managing:
- Multiple ad accounts (Google, Facebook, TikTok)
- Affiliate program logins
- E-commerce seller dashboards
- Outreach accounts on LinkedIn, Instagram, or email platforms
…then your browser fingerprint absolutely matters.
Modern platforms don’t rely on IP addresses alone to verify and track users. They use sophisticated fingerprinting systems—like FingerprintJS, ThreatMetrix, and proprietary tools—to collect hundreds of signals from your browser and device.
These include canvas rendering, WebGL data, screen resolution, timezone, language settings, and more. Even a minor inconsistency, like identical canvas hashes across multiple profiles or a WebGL vendor that doesn’t match your declared OS, can trigger suspicion or bans.
That’s where Pixelscan.net becomes essential. Instead of guessing how platforms see your browser fingerprint, Pixelscan shows you exactly what they might pick up—before you log into sensitive platforms.
On the other hand, anti-detect browsers like Incogniton are designed to give users true privacy and the ability to manage multiple browser identities without detection. They achieve this by spoofing your browser fingerprint, altering the data points that platforms use to track and link your online activities.
However, not all spoofing is effective. That’s why you should test each profile you create. Pixelscan allows you to audit your anti-detect browser setups in real time. With it, you can:
- Confirm that spoofing features are actually working
- Check for leaks or mismatches before using a profile
- Refine browser fingerprint settings to increase stealth
How to Run a Fingerprint Test on Pixelscan.net
Running a fingerprint test with Pixelscan is fast, simple, and requires no installation or login. Here’s how to do it:
Step 1: Go to https://pixelscan.net
Step 2: Click the “Start Check” button
Step 3: Wait for the scan to finish
Step 4: Scroll down to review the detailed results
The results are organized into categories:
- Time and Language
- Navigator
- Location
- Hardware Fingerprints
How to Interpret the Results
Unlike tools that assign a numeric score or badge, Pixelscan simply reveals what a detection system might see. It forces you to interpret your fingerprint holistically, component by component.
Here’s the key principle: you’re not aiming for perfection—you’re aiming for coherence. All the data points should tell the same story. When things don’t line up, Pixelscan will catch it—and real-world platforms likely will too.
Watch out for common red flags:
Identical Canvas Hashes Across Profiles
If multiple profiles share the same canvas fingerprint, spoofing isn’t working. Real users have subtle differences in rendering output.
Suspicious WebGL Vendor or Renderer
If your profile claims to be using macOS but the WebGL renderer shows a Windows GPU or virtual machine, that inconsistency can raise suspicion.
Accept-Language and IP Mismatch
For example, if your browser language is English (US) but your IP address places you in Indonesia, that may appear unnatural.
These inconsistencies might seem small, but when scaled across accounts, they form detectable patterns. Pixelscan helps you catch them early—before you get flagged or banned.
Using Pixelscan with Incogniton: A Tactical Guide
If you’re using Incogniton to manage multiple browser profiles, Pixelscan becomes your fingerprint debugger.
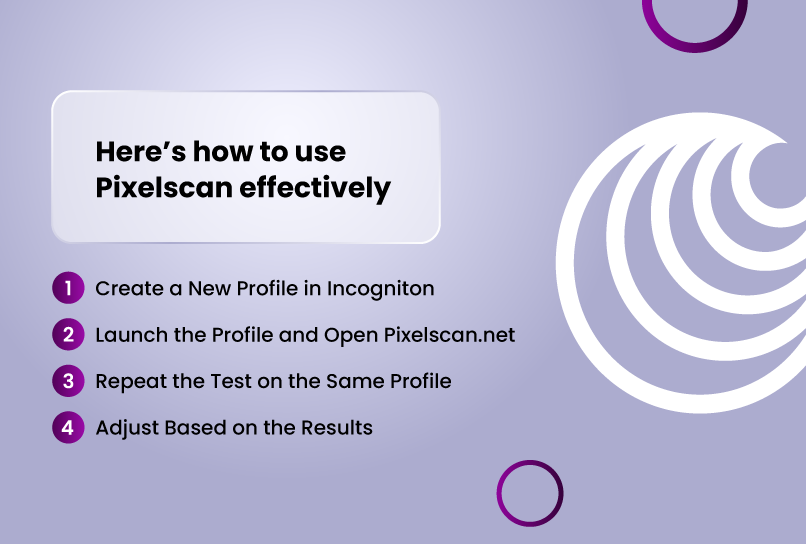
Here’s how to use it effectively:
Create a New Profile in Incogniton
Set your desired settings (language, timezone, OS, WebGL, etc.).
Launch the Profile and Open Pixelscan.net
Let the scan complete and take note of the fingerprint details.
Repeat the Test on the Same Profile
Run the scan multiple times without changing settings. If values like canvas hash, WebGL vendor, and timezone stay consistent, the profile is stable.
Adjust Based on the Results
Fix any mismatches or suspicious data points. Then retest to confirm that changes hold. This simple habit can drastically reduce your risk of detection when operating multiple accounts.
With Pixelscan and Incogniton used together, you can ensure each profile behaves like a realistic, isolated browser environment—boosting both your privacy and your operational success.
When to Use Pixelscan, and What It Won’t Tell You
Pixelscan.net isn’t a one-time-use tool. It works best when integrated into your broader browser hygiene and operational routine. If you’re using an anti-detect browser like Incogniton, think of Pixelscan as your first line of quality control before interacting with any platform that enforces fingerprint-based detection.
So when should you run a test?
- When setting up a new browser profile. Always test a fresh profile before logging into any sensitive platform. This gives you a baseline and helps you spot obvious inconsistencies.
- After making key changes to a profile. If you adjust canvas spoofing, timezone, WebGL, or language settings—test again. One setting can throw off the entire fingerprint.
- Before accessing high-risk platforms. Ad networks, e-commerce dashboards, affiliate portals, and email tools all use fingerprinting. Running a scan just before login can save you a lot of future problems.
- After a ban, restriction, or account flag. If something goes wrong, Pixelscan can help you isolate what your browser setup looked like at the time of the incident. Run a test, compare with other profiles, and look for anomalies.
That said, Pixelscan is not a complete detection simulator.
It won’t show you how a specific platform (like Facebook or Google) will respond to your fingerprint. Pixelscan states it doesn’t store your test results or simulate behavior—things like mouse movement, typing speed, or login habits, which platforms often monitor alongside fingerprint data.
Pixelscan also doesn’t warn you about reused or recycled profiles. If you use the same profile settings on ten accounts, it won’t alert you to that pattern, but platforms eventually will.
Use Pixelscan to check if your profile looks plausible. Use your own workflow discipline to keep things consistent and avoid reuse. Together, they’ll get you closer to staying truly anonymous on the internet.
Treat Pixelscan like a mirror. It won’t fix the problems—but it will show you exactly where they are.
Final Thoughts
If you use Incogniton or any other anti-detect browser to manage multiple digital identities, Pixelscan.net should be part of your setup routine, not an afterthought. It helps you catch the subtle mismatches and missing details that automated systems look for.
Things like inconsistent WebGL data, timezone-language mismatches, or a canvas fingerprint that’s too clean can all raise suspicion, even if your IP and proxy settings are solid.
Pixelscan doesn’t give you a score. It gives you a reality check. It shows you what platforms might see before they act on it. Use it to test new profiles, troubleshoot banned accounts, or audit your configurations before accessing sensitive platforms.
Remember, your browser fingerprint is part of your digital identity. Check it and make sure it is saying what you want it to say about you.
Frequently Asked Questions
Is Pixelscan.net safe to use?
Yes. Pixelscan.net runs entirely in your browser and doesn’t collect personal data or require a login. It tests what your browser exposes to websites by default—it doesn’t access anything beyond that. According to ScamAdviser, it is a legitimate website with a high safety score of 100/100. That’s so amazing!
Does Pixelscan store or log my fingerprint?
No. As of the time of writing, Pixelscan does not log results or store your fingerprint data. Each scan is session-based and cleared when you refresh or close the page.
Can I test multiple profiles quickly?
Yes. Open each Incogniton profile in a separate browser instance, visit Pixelscan.net, and run the scan. But note: Pixelscan doesn’t save past tests, so log results manually if you’re comparing multiple setups.
Does Pixelscan detect VPN or proxy use?
Yes, it does. While Pixelscan focuses on browser-level fingerprinting, it has a special tool called IP checker that you can use to test for proxy leaks, DNS issues, or WebRTC exposure. You can also use tools like Whoer.net or BrowserLeaks.com.
How often should I run a Pixelscan test?
At minimum:
- When setting up a new Incogniton profile
- After making any changes to canvas/WebGL/timezone settings
- Before logging into a sensitive platform (ads, affiliate dashboards, e-commerce)
- If you get flagged or banned and want to trace the issue
Is passing Pixelscan enough to guarantee I won’t get banned?
No. Pixelscan only covers browser fingerprinting. Real-world detection systems also analyze behavior (clicks, scrolls, login patterns), IP history, device reputation, and more. Pixelscan is necessary—but not sufficient—for staying undetected.
Can I automate Pixelscan testing?
Not easily. Pixelscan isn’t built for automated querying or API-based testing. It’s a manual tool, best used during browser profile creation and audit sessions.
Do I need to use Pixelscan if I already use an anti-detect browser like Incogniton?
Yes. Anti-detect browsers give you the tools, but not the feedback. Pixelscan shows you how your setup looks to detection systems. Without testing, you’re flying blind.
Can I use Pixelscan to test other anti-detect browsers like Multilogin or AdsPower?
Absolutely. Pixelscan works with any browser. The process is the same: open a profile, visit Pixelscan.net, review the flags, and adjust accordingly.
Anti-Detect Browser for Multi-Account Management
Manage unlimited virtual profiles for easy multi-account management. Safe and anonymous. Ideal for teams and individuals. Download and try for free now!